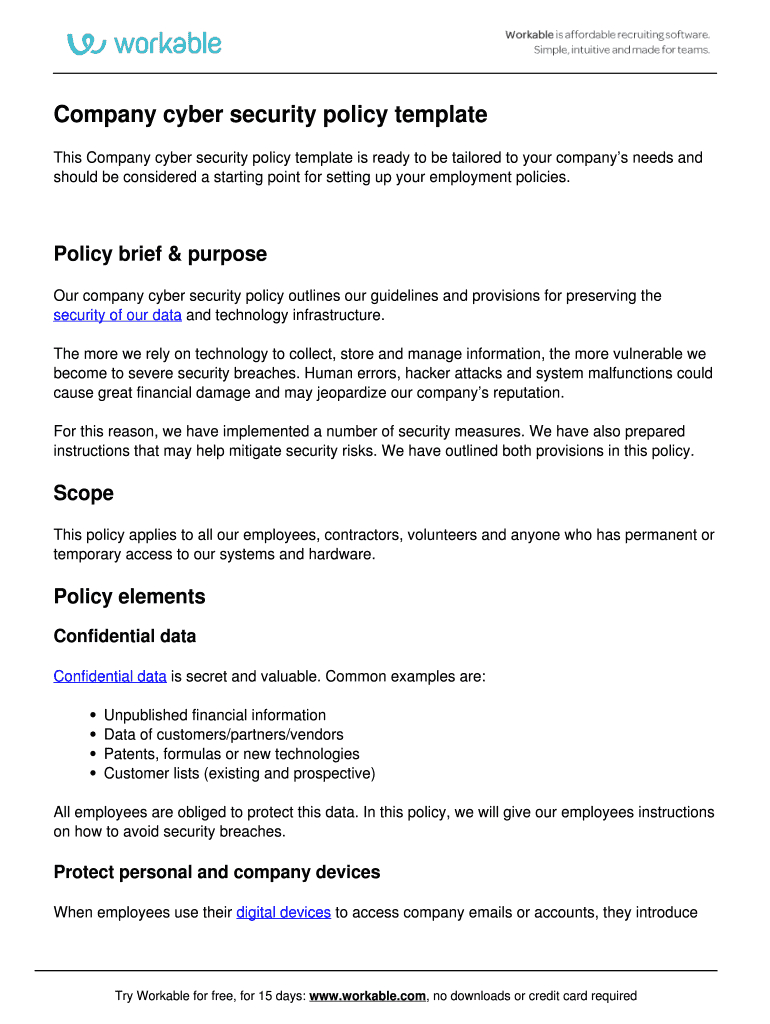
Are you looking to protect your valuable data from cyber threats and ensure the integrity of your IT systems? Look no further than our ultimate IT security policy template! With cyber attacks on the rise, it’s more important than ever to have a solid security policy in place to safeguard your organization’s information. Our template covers all the essential aspects of IT security, from password management to network security protocols, to help you create a comprehensive defense strategy against potential threats.
Safeguard Your System with Our IT Security Policy!
By implementing our IT security policy template, you can ensure that your organization is equipped with the necessary tools and guidelines to protect your data from unauthorized access and breaches. With clear and concise policies in place, your employees will have a better understanding of their roles and responsibilities in maintaining the security of your IT systems. From setting up firewalls to conducting regular security audits, our template provides a roadmap for securing your organization’s digital assets and minimizing the risk of data loss or theft.
Don’t let your organization fall victim to cyber attacks and data breaches – take proactive measures to secure your IT systems with our comprehensive security policy template. With our easy-to-use template, you can customize and tailor your security policies to suit the specific needs of your organization. By investing in IT security now, you can save yourself from potential headaches and financial losses in the future. Lock it down with our ultimate IT security policy template today!
Keep Your Data Safe with Our Ultimate Template!
Protecting your organization’s sensitive data is crucial in today’s digital age, where cyber threats are becoming increasingly sophisticated and prevalent. With our ultimate IT security policy template, you can take proactive steps to keep your data safe and secure from potential breaches. Our template covers a wide range of security measures, from encryption protocols to data backup procedures, to ensure that your valuable information remains protected at all times.
One of the key benefits of using our IT security policy template is its flexibility and adaptability to your organization’s unique security needs. Whether you operate in a highly regulated industry or have specific compliance requirements, our template can be customized to meet your organization’s specific security goals. By establishing clear guidelines and protocols for data protection, you can prevent security incidents and mitigate the impact of potential breaches on your organization’s reputation and bottom line.
In today’s interconnected world, data security is more important than ever. Don’t wait until it’s too late to secure your organization’s data – take proactive steps now with our comprehensive IT security policy template. With our easy-to-use template, you can create a robust security framework that will protect your organization’s digital assets and ensure peace of mind for you and your stakeholders. Keep your data safe and secure with our ultimate IT security policy template today!
Conclusion
In conclusion, safeguarding your organization’s IT systems and data is paramount in today’s digital landscape. With cyber threats on the rise, it’s crucial to have a comprehensive IT security policy in place to protect your valuable information from potential breaches and unauthorized access. Our ultimate IT security policy template provides you with the tools and guidelines you need to create a robust security framework that will keep your data safe and secure.
Don’t wait until it’s too late to secure your organization’s digital assets – take proactive steps now with our easy-to-use template. By implementing our IT security policy, you can minimize the risk of data loss or theft, protect your organization’s reputation, and ensure compliance with industry regulations. Lock it down with our ultimate IT security policy template and rest easy knowing that your organization’s data is safe and secure from cyber threats.


![security policy template 2024 download docx business in a box in it security policy sample template Security Policy Template 2024 [Download .Docx] | Business In A Box™ in IT Security Policy Sample Template](https://templatesamples.net/wp-content/uploads/2024/08/security-policy-template-2024-download-docx-business-in-a-box-in-it-security-policy-sample-template.png)

![42 information security policy templates cyber security e19085 throughout it security policy sample template 42 Information Security Policy Templates [Cyber Security] ᐅ throughout It Security Policy Sample Template](https://templatesamples.net/wp-content/uploads/2024/08/42-information-security-policy-templates-cyber-security-e19085-throughout-it-security-policy-sample-template.jpg)

 More Template Samples…
More Template Samples…
Disclaimer: All images on this website are the property of their respective owners. If you are the owner of an image and do not wish for it to be published on this website, please contact us. Upon receipt of your request, we will promptly remove the image in question.



